How to secure your accounts
It's more important than ever to protect your personal information and online accounts from cyber threats. That's why we've put together this article covering the steps you can take to keep your passwords safe and secure.
In this article, you'll learn about the importance of strong, unique passwords and how to create ones that are easy to remember but hard for hackers to guess. You'll also discover the latest password recommendations and best practices, including tips on how to use a password manager to keep track of your login credentials.
But protecting your accounts doesn't stop there! You'll also learn about the benefits of using multi-factor authentication (MFA) to add an extra layer of security to your online accounts. By requiring more than just a password to log in, MFA makes it much harder for hackers to gain unauthorized access to your sensitive information.
But, even with all these precautions in place, password breaches can still occur. That's why we'll also cover how to respond to a password breach and what steps you can take to minimize the damage.
By the end of this article, you'll have the knowledge and skills needed to secure your online accounts and protect your personal information from cyber threats. So whether you're a beginner or just looking to refresh your knowledge, we hope you'll find this article useful!
Part 01: The Importance of Your Passwords.
- Understanding the risks of weak passwords
- Why strong, unique passwords are essential
- The art of password management
Part 02: Modern Password Recommendations.
- Hard to hack
- Impossible to guess
- Easy to remember
- Easy to type
Part 03: Using a Password Manager.
- Downloading and installing a password manager
- Setting up the password manager
- Entering and storing passwords
- Using the password manager to sign into accounts
Part 04: Using Multi-Factor Authentication.
- Understanding how MFA works and its benefits
- How to set up and use MFA for your online accounts
- Using MFA to sign into your accounts
Part 05: Responding to a Password Breach.
- Preparing and practicing for a breach
- Responding to a breach
Part 01: The Importance of Your Passwords
With the exception to our health and the health of our family, few things are more important than our passwords. They are the keys to our kingdom. With them, we can access all our personal messages, photos, documents, banking information, and ever our work information too. They are the most important thing to keep safe and out of the hands of anyone else. Our passwords should never be shared, not even with loved ones.
"...few things are more important than our passwords. They are the keys to our kingdom...”
And yet, they can also be a real thorn in our side. Passwords expire, and we’re forced to think of new ones… but we don’t really. Most of us use variations of the same password over and over again. Many of us use the same passwords for many or all of our accounts across the internet.
This puts our most sensitive messages, photos, and banking information in peril, and potentially right into the hands of cyber criminals. Once one of these criminals has your password, all the accounts which share that password can be accessed within minutes with the use of a simple automated script.
Thankfully there is a better way. We can create long, complex, easy to remember, and easy to type passwords. We can create unique passwords for every account, and manage them easily with a few simple guidelines and the help of some extra secure software.
In this article we’ll be diving deep in the art of password management. We’ll have some practice exercises and homework throughout these sections. This topic is absolutely essential and foundational to your online security. If your passwords are easy to hack, any additional security or safety added on later can just be bypassed.
Master your passwords, and you’ll find your daily life using your computer and all the various accounts you access will become easier and safer.
Part 02: Modern Password Recommendations
Overview
The software juggernaut Microsoft recently released a paper recommending a fundamental change to how companies have been enforcing passwords. Many companies have been forcing users of their systems to change their passwords frequently. It turns out this is annoying and forces us to use simple, easy-to-remember, and easy-to-hack passwords passwords, so we can continue doing the work we need to do.
We can do better. We need passwords that are:
- Hard to hack
- Impossible to guess
- Easy to remember
- Easy to type
Let’s examine each of these to determine how we can accomplish them.
Hard to hack
In 2018 the massively popular photography website 500PX suffered a data breach. Usernames, password hashes, and personal data were stolen by hackers, and then sold on the black market for profit. The users of 500PX’s services were not at fault here, rather 500PX themselves suffered a breach and leaked information for more than 14 million users. Those who had a simple, easy to guess passwords may have suffered account hacks, whereas users who had secure passwords may have been spared, but why? And what makes a password hard to hack?
To answer that, let’s examine that “password hash” I mentioned above a little closer. When a hacker breaches a company they often times don’t get password in a readable form, instead they get a jumble of letters and numbers called a “hash.” Hackers have to use a powerful computer to try to covert these hashes into a readable password - and it’s this process we are trying to make as painful as possible for hackers.
The most effective way to make passwords hard to hack is by making them long. Consider making you important passwords at least 16 characters in length. The second most important way is to make them complex, ensuring you’re using capitalization somewhere, a number, and a special characters. Complex passwords make it harder for hackers to guess the password because rather than just using the 26 character alphabet (assuming your password in English), they need to use all the character - 95 or so.
"The most effective way to make passwords hard to hack is by making them long."
In this exercise we're going to use an online tool to get a feel for how long passwords need to be in order become difficult to hack. Check to see if your passwords have already been breached and how long they will take for someone to crack!
- Open this website: https://nordpass.com/secure-password/
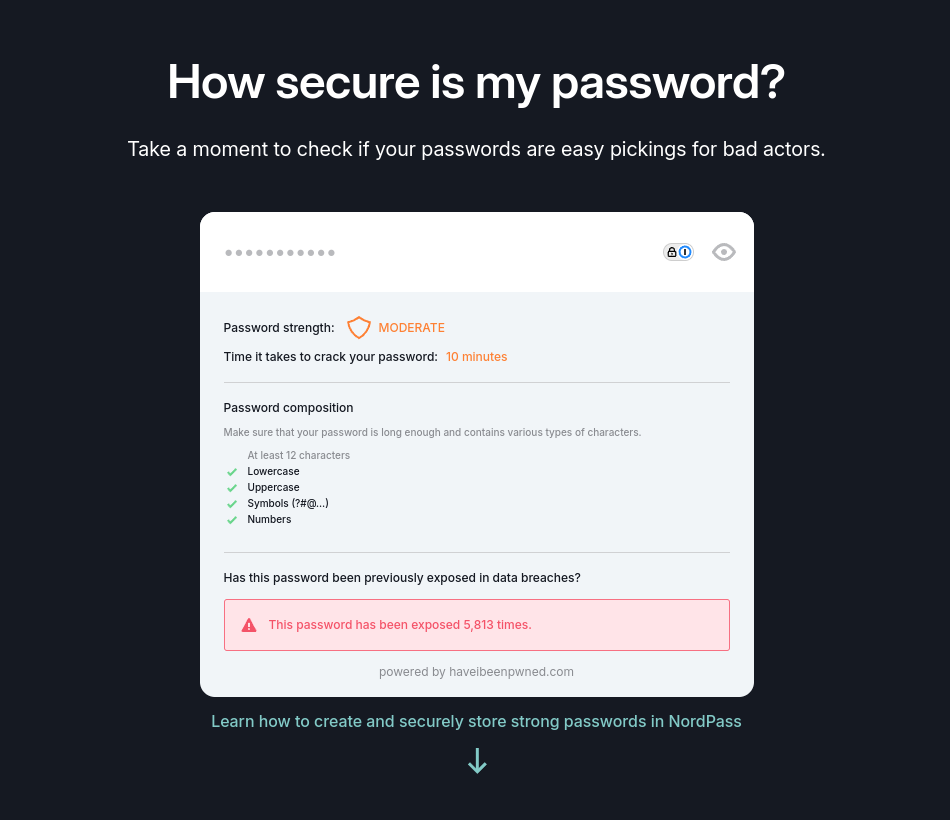
- Click the “No, use the online strength checker” button
- Enter a few simple passwords and watch what happens to the calculated time it will take a hacker to get it. Typing a fairly long, yet complex password like “Welcome123!” only takes 5 minutes to hack.
- Try entering a variation of your passwords to see how secure they really are. We’re looking for it to take years to hack
How much time will it take to crack your current passwords? How long do passwords need to be in order to take centuries to crack?
Impossible to guess
Lets look at the case of the 2015 US federal tax refund scam. The IRS had just created a new option when submitting a tax refund - a sort of forgot password option, where one could answer a series of personal questions to verify the identity and then claim the tax refund. The problem was the answers to many or all of the questions were freely available online from social media posts.
It wasn’t long until people across the country started reporting fraudulent claims for their tax refunds.
Hackers often scour social media, photos, and any leaked data in order to make educated guesses about what passwords may be. For this reason we must avoid using things like seasons, important dates, children’s names, pet’s names - any piece of information about yourself that has been shared with someone else.
Easy to type
Let’s think for a moment about what it means to use a long 16 character password every day. We use passwords a lot - when we log into our computers in the morning, log into webmail, social media, etc. If we have a long password that’s hard to type, that will be a big problem to type frequently. Sometimes we need to type our passwords on the small screens of our phones, or even video game consoles, so they need to be easy to type.
To address this, let’s use words in our passwords to help ensure they aren’t too bad to type across all our devices.
Putting it all together
Ok, so how to do we create these hard to hack, impossible to guess, easy to remember, and easy to type passwords?
- Let’s open this website and see what happens: https://correcthorse.pw/ . This website will randomly give us a bunch of words to work with. If nothing stands out to you, click the generate password button to get a new group of words.
- Let this be the inspiration for you to choose three or four of the words that make a memorable image in your mind.
- Now, take the spaces or dashes between the words and replace them with other special characters.
- Finally, place a number either at the beginning, between words, or at the end of the password.
We now have a unique password we can remember, is complex, long, and easy to type since it’s mostly just words. More importantly, we now have a way to create new secure passwords going forward.
Examples
Ok, I need to reset my work password again, but this time I want to be more secure. So, I open the https://correcthorse.pw/ website and see what it gives me. I see a few words that can go together - ‘dark’ and ‘red,’ but none of the other words stand out to me. I click on Generate Password to generate more words and I see ‘slow’ and ‘laser’ comes up. An image of a Star Wars like red laser comes in the my and I think I can remember that.
I reorder the words to make sense to me, and I capitalize some of the words but not all. Finally I add some special characters and a number, and I have:
Dark!red!slow!laser8
Bingo, that’ll last me a while. Plugging that into the password strength calculator and I see it’ll take hundreds of years to hack - exactly what I’m looking for.
What image or memory mnemonic did you come up with to help remember your secure password?
Part 03: Using a Password Manager
But, there’s a pretty big problem with using unique passwords for all your accounts – how do we remember all these unique, completely different passwords? (hint – with some helpful software)
What if instead of remembering every password, we only needed to remember two:
- One password to log into your computer
- One password for your password manager software
For example: when signing into your online billing portal, instead of typing the password for that site, we open the password manager and copy the password, then paste it into password box. With some practice, managing dozens of unique passwords will become easy, and you’ll gain a little bit of your sanity back.
There are a surprising amount of password managers available today, but for this lesson we’ll be using a free, open-source, and highly trusted password manager called KeePassXC. This small application will give all the basics we need to understand how these apps.
Getting KeePassXC downloaded and installed.
- Open this website: https://keepassxc.org/download/ .
- Click the installer for the latest version available to start the download.
- Once downloaded, click the installer from your browser’s downloads list to run it.
- Accept the default settings during the installation, clicking next when needed, and finish at the end.
Setting up your Password file
KeePass securely stores all your password in a file located on your computer. This file uses strong encryption to protect itself from prying eyes.
- Let’s start KeePassXC and then click the “Create a new database” button on the main screen.
- Next, name your password file whatever you would like – I’m entering “Personal Passwords” here, then click Continue.
- On this screen we can and change the encryption settings if needed, but the defaults are fine, so lets click on Continue again.
- Now it’s time to enter a strong, unique password – like the one you made in our last section, then click Continue.
- Finally, let’s select a location to save our passwords file – like your Documents folder, then click Ok or Save.
KeePassXC is now ready to use!
Entering your first passwords into KeePass
Now that we have our password manager installed, it’s time to start entering some passwords.
- With KeePass open and logged in, click the New Entry button in the top toolbar.
- Let’s start by entering your primary email account. In my case I’m entering a Gmail account. Enter the name of your email service, your username, your password, and the website of your email service.
- Click OK to save the password.
Using the password manager
Lets take this a step further – was the password for you primary email account unique and secure? If not, now is perfect time to use what we learned in our last lesson. Let’s use KeePass to log into our email account now, secure our password, and update our entry in KeePass.
- Right-click on your new password entry and click “Open URL” . This will open your web browser right to the website we specified when we created the entry.
- With the web page now open, navigate to the login page
- Now, instead of typing the username and password, return back to KeePassXC, right-click the password entry and select “Copy Username” . Return back to the website, and paste it into the username.
- Repeat this for the password. NOTE, KeePassXC is able to make this easier by using the keyboard (the shortcuts can be seen in the right-click menu). KeePassXC also has an autotype feature, which will type the username, then press Tab, then enter the password, then press enter automatically. This will work for most websites and applications.
Making Your Password Manager Work For You
Now that we have a basic understanding of how to use a password manager, it’s time to put it to good use and get a lot of practice using it. I’m asking a lot here – a fundamental change in how you sign into all of your accounts – a change in some of the most foundational things you do on your computer.
You will very likely find this exercise to be very annoying at first. It has a learning curve and will be slower to log in for a while, but with practice using a password manager will be faster – and in time all our accounts will be using unique and secure passwords.
This exercise is intended to get you started with your most common accounts to be secured, but will be ongoing from now on! Do this exercise for any accounts you’re signed into right now, and keep doing it every time you need to sign into an account.
From now on...
- Whenever you need to sign into any website or application on the computer, open your password manager and search to see if that account is present. If it is, use the password manager to sign in instead of manually typing the username and password.
- If the account is not present in the password manager:
- Sign in manually, then change that account’s password to a unique secure password
- Add the account to your password manager with the URL, username, and password information.
- Use the password manager to access the account from now on.
Part 04: Using Multi-Factor Authentication
Now that we’re using strong, unique passwords for our accounts, and we’re slowly (or quickly depending on motivated you were in the last exercise) ensuring all our accounts are using unique passwords, and we’re now using a password manager, surely that’s enough to finally be secure right?
Umm… No. Sorry.
Strong passwords make it difficult for hackers to figure them out. Unique passwords limit the damage done when a password does get compromised, but neither actively prevents hackers from accessing your account – they just slow them down.
Thankfully though, not all of our accounts are sensitive. Think about all the accounts you’ve been adding to your password manager. Some of those accounts, for example your personal email accounts, can be used to reset the passwords for other accounts. Some of those accounts can access your credit cards or banking information. Some of those accounts contain personal pictures of your family and loved ones. It’s these accounts we want to protect with another layer of security; we want to actively prevent hackers from ever gaining access to them.
This is where Multi-Factor Authentication (commonly referred to as MFA) comes in. MFA verifies the person not only knows something to sign in (like a password), but also has something (like a phone or a token). In this way, MFA successfully blocks 98% of all hacking attempts. Even if a hackers compromises a password, they still don’t have the thing (your phone or token) needed to sign in.
Some examples of sensitive accounts that should have MFA enabled:
- Personal email accounts
- Amazon and shopping accounts where credit card information is saved
- Ebay
- Paypal
- Banking sites
- Investment sites
- Facebook, Twitter, and other social media websites
- File sharing or photo sharing services, like Dropbox, Box, or Mega.
Setting up MFA
Not all services offer MFA. If one of your sensitive accounts does not have MFA available, please consider changing services. It may be a bit of a pain now, but dealing having your bank funds drained, or having malicious messages sent to all your friends on social media is a lot more of a pain.
When setting up MFA we typically have two choices available to us. We can have a special number sent to our phone as a text message, or we can use an app to generate the special number. Whenever possible we should use an app on our phone because text messages can (and are sometimes) intercepted by hackers.
Once MFA has been set up, when accessing that account you’ll be prompted for your password as normal. We can use our password manager for that. After entering the password, we’ll then be asked for the special code – often called a One Time Passcode (or OTP for short). Here, we’ll look at our phone and enter the number given to us in a text message, or in the app we’ve configured.
In this exercise I would like you to follow along with setting up MFA on your personal email account. Throughout this exercise I will be using Google as an example, because gmail is very popular right now, and it does support MFA. I’ll also be using the Google Authenticator app on my phone, again only because it’s quite popular, and does work quite well.
You may not be using Google services, so the exact steps you need to take may vary a little, but generally they should be very similar.
- Sign into your personal email account using your password manager.
- Open your account settings and locate the security or login settings.
- Enable MFA (also sometimes 2 Step Verification, or 2FA)
- Configure a token on an app, or enter your phone number to receive a text message
- Once enabled, log out of your email
- Sign in again and enter your password when prompted, then enter the MFA code when prompted.
- Repeat this exercise for all your most sensitive accounts such your primary personal email address, financial websites, and shopping websites where your credit card information is saved.
Were you able to enable multi-factor authentication? What accounts have you enabled it for?
Using MFA when signing in
- Use your password manager to open the needed website.
- Use your password manager to copy and paste the username and password.
- You will then be prompted for MFA. Check your mobile phone. You may have been sent a push notification and if so, tap Approve.
- In the case you're prompted to enter a code, open the MFA app, tap on the token and enter the code presented on the screen.
Part 05: Responding to a Password Breach
OK, so we have a password manager, we're filling it up with unique secure passwords, we're enabling MFA on our most sensitive accounts first and as many others as we can afterward... We're pretty much immune to password and account hacks right?
Nope.
Even with the all the additional security we've been practicing, an account breach is still inevitable. This isn't because if you - you've been working hard to prevent this and by following the advice shared in this article you've dramatically lowered the chances of being breached. The issue is with the companies you have accounts with.
Think about it, why would a hacker spend hours or days trying to breach one person's account when they can spend the same amount of time and possibly breach thousands of accounts at a time?
So, we must assume our account passwords will eventually be leaked and breached. And if we assume our accounts will eventually be breached, then it makes sense to prepare for this inevitability. By preparing and practicing for a breach we will be able to reduce the impact of the breach as much as possible.
Preparing for a breach
- The good news is, you've already started to prepare by resetting your old insecure passwords to long, secure, unique passwords, and then storing those unique passwords in a password manager so you don't need to memorize every one. By using unique passwords for each account, you're reducing - segmenting - collateral damage caused by a breach.
- You've also been preparing by enabling MFA on your most sensitive accounts. With MFA enabled, if your password is breached, attackers still cannot access your accounts because they also need the code or a notification approval from you directly. If you suddenly start to receive MFA notifications and you're not attempting to sign in, that an indicator you need to start responding to a breach.
- In addition to what we've practiced so far, we need to train ourselves to recognize attacks such as smishing, phishing, and scamming. These are the most common and effective ways attackers trick us into giving up our passwords. These attacks are even used to bypass MFA, making it critical for us to identify when we're being attacked.
- Backup your computer and data. In the case you are attacked, breached, and infected with malware - your data may be used against you. For example, malware can capture your browser cookies and use those cookies to access your accounts and even bypass your MFA. Or your data can be encrypted and an attacker can demand you pay them money in order to get your data back. By having a backup of all your data, and practicing how to restore from that backup, you can simply wipe your computer or device and restore what you need from your backup.
- Monitor dark web breach websites and tech news for account breaches and large data leaks. If you see one of your accounts as part of a breach or data leak, it's time start responding to a breach.
- Ask your friends and family to alert you if they ever see unusual messages or posts from your accounts.
Responding to a breach
OK, you've been alerted of breach, or you suspect a breach may be occurring. What do we do?
- Attempt to sign in to the account.
- If you're not able to sign in, and not able to use the "forgot password" option to gain control again, you may need to work with that company's support team to gain control of your account again. In this situation, you may need to go through additional identity verification with the support team.
- Once signed in, change your password to a long, complex, unique password as we discussed in our previous lessons.
- Enable multi-factor authentication on this account to avoid another breach.
- Wait about 10 hours or so.
- Reset you password again to a different long, complex, unique password.
If it's possible your computer has been infected with malware, perform the above steps from a different device, such as your mobile phone. If the password that was breached was an old insecure password that was used on multiple sites, immediately start repeating the above procedure for each account that shared the same password.
If you suspect a computer has been infected with malware, start your malware respond and recovery response (covered in a separate article).
If you suspect a friend or family member's accounts have been breached, call and speak with them to alert them of the issue. For example, if you've started to receive Facebook messages from a friend request you send money, or click on a malicious link. You may need to help them with their breach, or send them a link to this article.
Once you're in control of your accounts and their passwords have been changed, take some time to review how the password breach occurred.
- Were you targeted and breached specifically, or was the company hosting the account breached?
- If you were specifically targeted, can you determine who was behind the attack? For example, was this someone who you previously knew and trusted, or was this the work of a random hacker?
- Can you determine why this breach occurred? Was is simply part of a larger attack? Was the attacker trying to extort money from you?
Trying to answer these questions may reveal additional steps you can take to prevent another similar attach, or perhaps people you thought you could trust can no longer be trusted.